Human-Centric Systems Thinking & Doing, in this Digital Age
Over-dependability on Undependables
People, society, public and private sectors have become over-dependent on undependable systems. It has exposed us to increasingly deteriorating levels of sovereignty and other meaningful control – putting all eggs in one or two baskets –. This trust we have given away ourselves, for whatever reason but generally not for the right reasons. Now it has clearly shifted to growing levels of mistrust.
However smart and otherwise advanced one may want to market the current phase of this Digital Age and however we would love to trust it, it has proven not to be immune to evil, build-fast-fix later business models, ignorance, stupidity, no-free-lunch services, intentional information asymmetry and other breaches of values and norms, including breaches of public trust and trust by individuals.
These threaten systems, services, lives of people, key networks and even entire nations, democracies, and societies. And, both the malicious actors including the robber baron’s of the current first part of this Digital Age do not work alone. They have joined forces, they exchange collected or derived data, and they are winning.
Bring Back the Integrity of Trust
All in all, it further erodes trust. It also hinders our ability and need to focus on societal challenges of this 21st Century (both in the physical, cyber-physical and cyber world), and for that deploy all means that we have, including strategic, operational and financial means, and most of all our human intelligence, willpower and our ability to collaborate, build communities and make things work. Without us trying to counter these currently unfavourable developments, we will remain part of the problem, helping to increase it day-by-day.
The term trust is and has been misused too often. Its integrity is lost. So, we need to bring back the lost integrity of trust, and defend and sustain it. Although not an easy feat, it is a prerequisite for being able to lead, use and being in meaningful control of the next phase of this Digital Age. For this, we need an holistic, system thinking approach and system doing attitude.
Make it Work
In most cyber-physical and other digital systems, trust components such as safety, security, privacy, data protection, transparency, accountability and many other ‘non-functionalities’ are seldom being into account. What if a device, system or service does not work as intended, as expected or as actually used?
Cybersecurity, safety, privacy but also digital sovereignty, data protection, transparency, accountability, resilience, trust and trustworthiness are examples of non-functionals that should, by design and by default, be part of any truly ‘working’ application, technology, product, system and service.
These non-functionalities are generally still seen as a mere after-thought; a seemingly engineering and manufacturing nuisance and cost-adding factor. However, given the pace at which technology has developed and is developing, these non-functionals are not nice-to-haves anymore.
These are essential trust components, and they are absolute need-to-haves; by universal values, ethics and accountability, and nowadays (although quite late) more and more by the Rule of Law. Without them, there will be no trust, no trustworthiness, and no future-proof digital ecosystems.
Make IoT Work
From now on, we need to – only and consistently – design, create, market, implement, update respectively procure, deploy, use, monitor and sustain cyber-physical or other digital systems that work, not merely function.
Making IoT work, with the relevant, contextual trust components and trustworthiness capabilities as essentials and as enablers (so not anymore as problems) is in my view what project ARDACIAN-IoT is all about.
With the spirit and executing power of the project such as ARDACIAN-IoT and its consortium and network, I am sure we can jointly build IoT ecosystems that actually work, with useful functionalities and relevant non-functionalities included by design, monitored when deployed, and continuously double-looped and optimised during and after – also for new useful by-design functions and features, without function creep –.
IoT should bring progress for people, society and planet; not trigger more mistrust, loss of sovereignty or undermining of democracy (being self-sovereignty, data sovereignty, community sovereignty, open democracy, and that of member states, union, allies and friends).
ARCADIAN-IoT Use Cases & State of the Art
When one closely assesses the three (3) main cases that ARCADIAN-IoT is developing (industrial control systems, personal safety aid, and tele-medicine) on which, where, how and to what extent those non-functionals are used, balanced and embedded in those use cases, one the main notable features it that identity is mentioned in each, as an apparent essential dimension. Identity of objects, identity of communications, identity of persons, and the authentication and protection of each thereof. This is for sure an essential state of the art trust component, in this case being an all-present trust dimension.
Obviously, there are many other trust components, and in the ARCADIAN-IoT use cases descriptions one sees many explicitly mentioned and otherwise taken in already.
The right, dynamic set of combined trust components – each with the contextually relevant ones included – is what brings back and caters for integrity of trust.
N-Dimensional State of the Art (SOTA), End to End Digital Ecosystems
Combining the vast domain of trust components within even vaster IoT ecosystems (sometimes connected/centralised, interconnected/decentralised, hyper-connected/distributed and sometimes already even unconnected/autonomous) is a necessity. Yet, it is quite complex and difficult to grasp and comprehend.
In order to come to workable and actionable frameworks and models to address the pre-requisite trust and trustworthiness components of for instance security, privacy and data protection in IoT, and to assess which technical and organisational security measures it needs to consider and implement, various organisations in the public sector and private sector, as well as academia, NGOs and others, have set up committees, taskforces, conferences, workshop-driven developments and consultation proceedings.
Within the European Union these have been or are being codified more and more into principle-based frameworks that aim to coming to or towards mandatory levels of appropriate dynamic accountability, as for instance set forth in the General Data Protection Regulation (GDPR), Radio Equipment Directive (RED) with its 2021 Delegated Act for Connected Product, 2021 Medical Device Regulation (MDR), revised Payment Services Directive (PSD2) with its Regulatory Technical Standard (RTS), and upcoming revised Network Information Security Directive (NIS2), Digital Governance Act (DGA) and the Digital Services Act (DSA), to name a few.
The last decade this has further resulted in several hundreds of public, industry, societal and public-private IoT-related initiatives, frameworks, recommendations, standards, best practices and other guidelines on state-of-the-art level non-functionals in IoT. Although one may think it is leading to fragmentation, the various sets of publications consist of hundreds of trust components and related principles that can be extracted, combined, loaded with context and used for the benefit of any human-centric IoT device, system or service. So, this particular fragmentation can be seen as an enabler, as it democratises and distributes efforts, use and outcomes.
To date, we have found more than 500 unique trust components that are relevant for IoT and in IoT ecosystems. With these, one can make any desired or required risk mitigation, chemical reaction, intertwined physics structure and therefor any desired and trustworthy human-centric dynamic IoT devised, system or service.
In order to address this, a N-Dimensional State of the Art (SOTA) model has been developed to identify, segment and at a high level categorise relevant technology, stakeholders, data (classes) and context, identify data flows, segment the technical stack, risk and impact on relatively high level, same as the relevant dimensions, structure, contextualize and heat-map the above, and address interdependencies, conflicts, resilience, impact and possible trade-offs. This model can be used as the basis to discuss and address non-functionals and related principles in cyber-physical and other digital ecosystems.
When one structures and analysing these, one can for instance segment it from the perspective of four (4) main (more or less technical) layers and three (3) main dimensions. Each dimension may be relevant in one, more or even all of the layers.
The four (4) main layers are the following:
- Service
- Software/Application
- Hardware
- Infrastructure/Network
The three (3) main dimensions are the following:
- User/Human
- Data
- Identities & Authentication
These four main layers and three main dimensions can be visualized as set forth below.
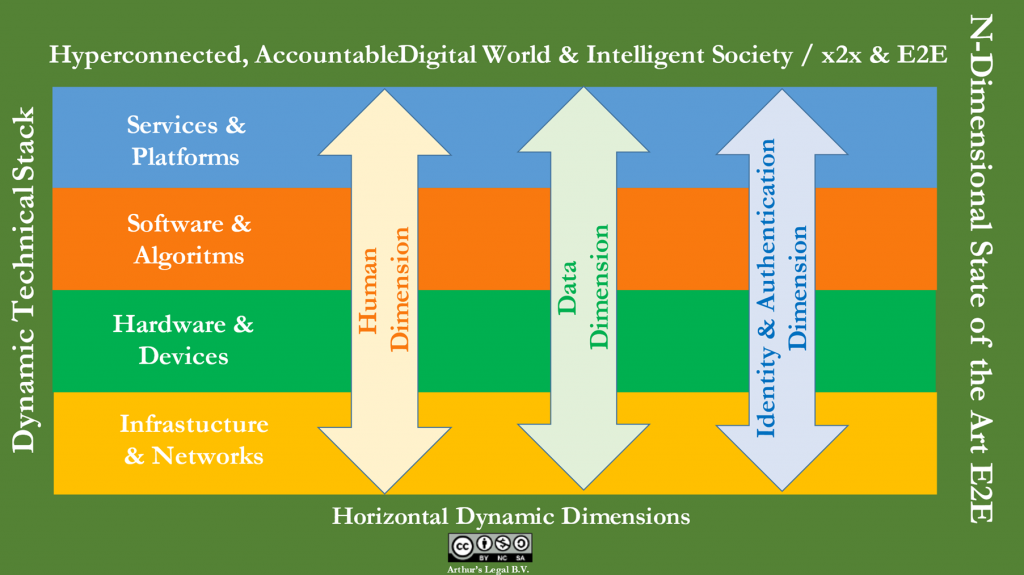
The N-dimensional aspect of this model can for instance be seen when each of the four layers would be applicable and relevant in a digital ecosystem, and each of the three dimensions are applicable and relevant as well in each of those layers. This would accrue to 12 dimensions already. There can, however, be less or more dimensions in play, depending on the particular use case, application and context. The various ARCADIAN-IoT use cases demonstrate that.
When taken the perspective of certain connectivity of the IoT device, system or service, the N-Dimensional SOTA model would accrue to various schemes that could for instance, for example, constitute the following:
Non-connected: 6 dimensions, when segmenting the layers and dimensions as follows:
Two (2) main layers
- Software/Application
- Hardware
Three (3) main dimensions:
- User/Human
- Data
- Identities & Authentication
Connected: 12 dimensions, when segmenting the layers and dimensions as follows:
Four (4) main layers:
- Service
- Software/Application
- Hardware
- Infrastructure/Networks
Three (3) main dimensions:
- User/Human
- Data
- Identities & Authentication
Inter-connected: 15 dimensions, when segmenting the layers and dimensions as follows:
Five (5) main layers:
- Service
- Software/Application
- Edge Devices
- Communication Networks
- Computing Infrastructure
Three (3) main dimensions:
- User/Human
- Data
- Identities & Authentication
Hyper-connected: 15 dimensions, when segmenting the layers and dimensions as follows:
Five (5) main layers:
- Service
- Software/Application
- IoT Devices
- Communication Networks
- (Additional, Decentralised) Computing Infrastructure
Three (3) main dimensions:
- User/Human
- Data
- Identities & Authentication
The segmentation and structuring as set above obviously is not the only one possible. Various other segmentations are to considered as well, such as for instance real-time, near-real-time or not. Other segmentations that can be considered are fixed/unmovable IoT (such as in the ICS use case of ARCADIAN-IoT) or personal/movable IoT (such as in the other two use cases), single-vendor or multi-vendor, OEM, public, private, public-private, et cetera.
Risk Classification Spectra: A Multi-Layered Approach
If one wants to think and talk about trust in a sensible way, one needs to think and talk about risk. Otherwise, one can never walk the talk.
When looking at the above-mentioned hyperconnected IoT devices (sub d, above) and taking a risk-perspective to those, a methodology to do high-level quality risk classification is to have a multi-layered approach and do such risk classification per spectrum, starting with the risk classification of the connectors and connectivity of the IoT device itself.
It is essential to understand the various risks that are embedded in or could arise from such IoT device. Subsequently, other risk spectra should be considered and risk classified, as visualised below.
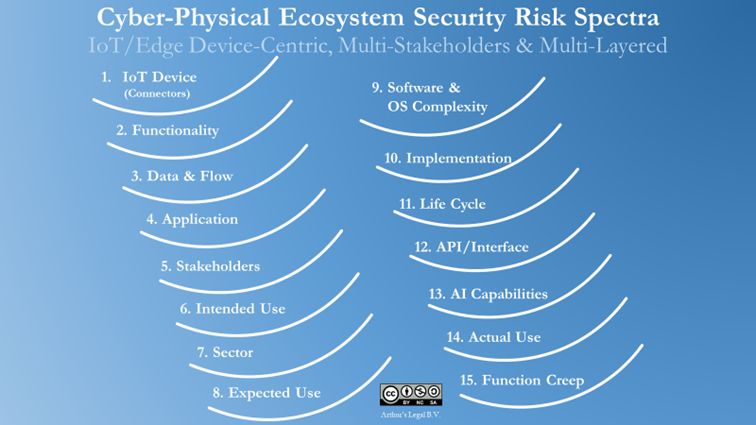
Regarding risk classification, in most situations, sectors and markets three (3) categories of main risk levels are used: basic/low, substantial/medium and high. These are also generally used in applicable regulations, standards and other policy instruments, also within the European Union.
Based on the outcome of (i) a risk classification for each spectrum, and (ii) the interim outcome of each risk spectrum as well as the holistic, combined outcome of the risk classifications from Spectrum 1 (Connectors) through 15 (Function Creep), the applicable, dynamic baseline risk classification can be established.
Based on that applicable baseline, the holistic, system perspective constitutes the combined risk classification on which one can consider, organise and implement technical and organisational measures to take in and balance out the relevant trust components.
As per the dynamics of IoT and IoT ecosystems, any of the risk classification spectra can be expected to trigger, change or otherwise show relevant dynamics, such as (A) technical or other threats and vulnerabilities, (B) actors and other stakeholders anomalies, updates or upgrades in code, datasets or attributes, or (C) changes in regulatory standards, policies or other relevant best practices, it is recommended to double-loop as well, including those spectra that are or may be related or otherwise are (inter)depended on the particular spectra. Therefore, it is recommended to continuously monitor the risks, and where necessary or otherwise double-loop thereafter to keep the security measures up to date and resilient.
The Five T’s
Trust and the integrity of trust can be catered for in many ways, including by demonstrating trustworthiness and accountability, both before, during and after deployment and use of any IoT device, system or service.
In this article we have (relatively briefly) touched on a few of the ways to (re)build trust, including (A) identifying the contextual and dynamic trust components, (B) segmenting and structuring in order to help taxonomy, common understanding, appreciation and orchestration, (C) focusing on holistic life cycle thinking, design, deployment and dynamic assurance, including continuous monitoring, optimalisation and accountability, also with the notion that trust equals consistency over time.
All this, to be able to create, build, nurture and cater for interdisciplinary human-centric, transparent and trustworthy digital means, as an aid for individuals, communities, society, economy and planet, that respect and protect the human values of each person.
This can be summarised and sequenced with five (5) T’s: Taxonomy, Transparency, Trust, Transformation and Trustworthiness, as visualised below.

If we do this right in projects such as ARCADIAN-IoT, in my view we have a global market of about eight (8) billion individuals that we can help to improve their quality of life with the above-mentioned five (5) Ts as the unique selling point. For once, this next generation of IoT devices, systems and services can scale and succeed to levels of great affordability, resilience, durability and (economic, societal and ecologic) sustainability. And, each will always have the main trust principle in its DNA: the Principle of No Surprises.
December 2021. Blog by Arthur van der Wees, Managing Director of Arthur’s Legal, Strategies & Systems, Amsterdam, Security Advisory Board Member as well as Ethics Advisory Board Member of ARCADIAN-IoT.